Single Sign-On
Getting Started
Before configuring SSO with SAML, you'll need:
- A SAML Identity Provider that you can connect with Cloudsmith.
- Manager access to the Cloudsmith organization.
Supported Providers
Whilst Cloudsmith should work with any generic SAML IdP, we officially support and provide documentation for a number of the most common providers. Please see the below for guides for each officially supported provider:
Other providers may be supported if they can set up a generic SAML application. If you need help with an unlisted integration, you can still contact us!
SAML Landing Page (Login)
Once configured, you'll be able to access the SAML login page of your organization at the following URL:
https://cloudsmith.io/orgs/{ACCOUNT}/saml/login/
Where ACCOUNT is your organization's slug/identifier (what you would normally see in the URL when accessing your organization within Cloudsmith). If you're not sure what this is, just ask us.
Enable SAML
You can enable SAML in your Cloudsmith organization settings:
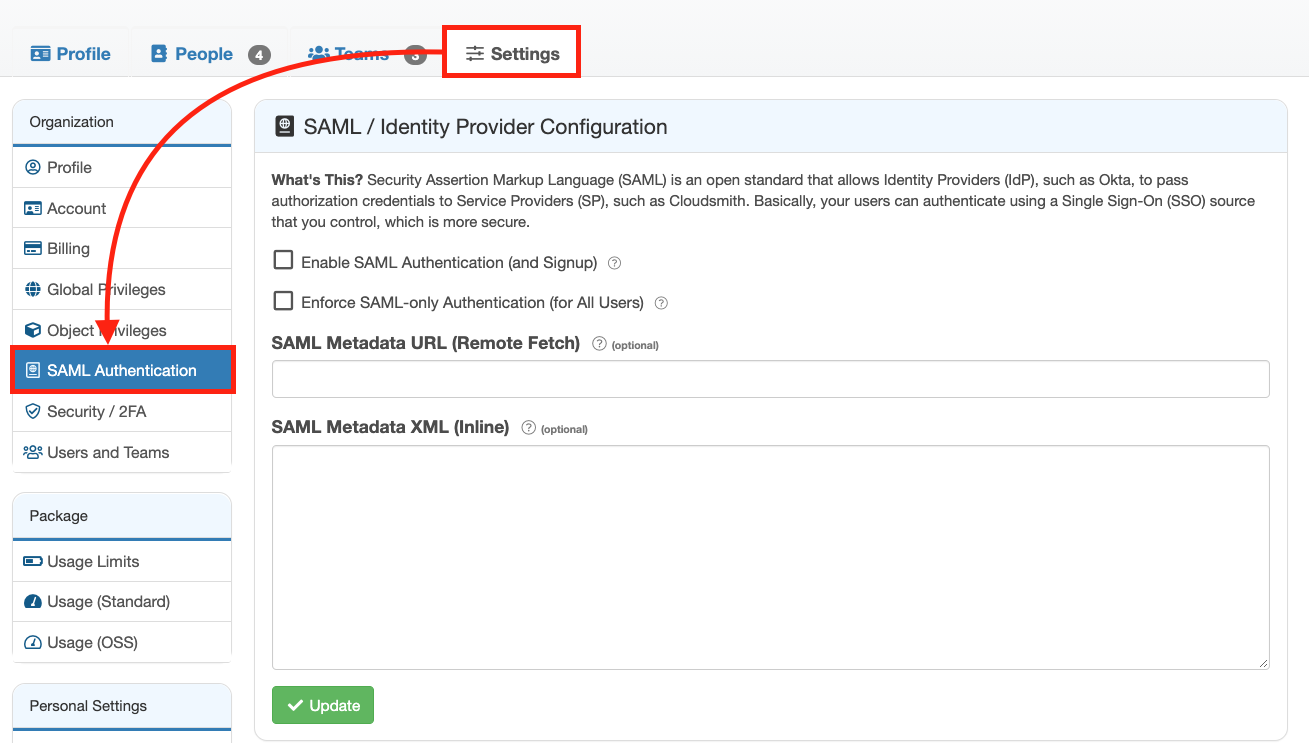
SAML Authentication Setup
You just need to provide your SAML Metadata XML. You can provide the Metadata XML via a URL, or by copy/pasting the Metadata XML from a file directly inline in the form
You can then enable SAML and optionally choose if you wish to enforce SAML-only authentication.
If you choose to enforce SAML-only authentication all users that belong to this org will be forced to authenticate via SAML-only, in order to access Cloudsmith. They will not be able to use password-based authentication or other social auth providers. This is more secure, but use caution to prevent lockouts.
SAML Group Sync
NOTE Please do not enable SAML Group Sync before creating your group mappings, as SAML Group Sync will remove any users from a team if there is no corresponding group mapping present.
SAML Group Sync is used to use map an attribute from your Identity Provider to a team in your Cloudsmith Organization. This allows you to add users automatically to the team.
Creating a Group Mapping
You first need to create mappings that will define which attributes and values will map to the respective teams in your Cloudsmith Organization.
To configure a new mapping, click the "Create Group Sync Mapping" button under "SAML Group Sync":
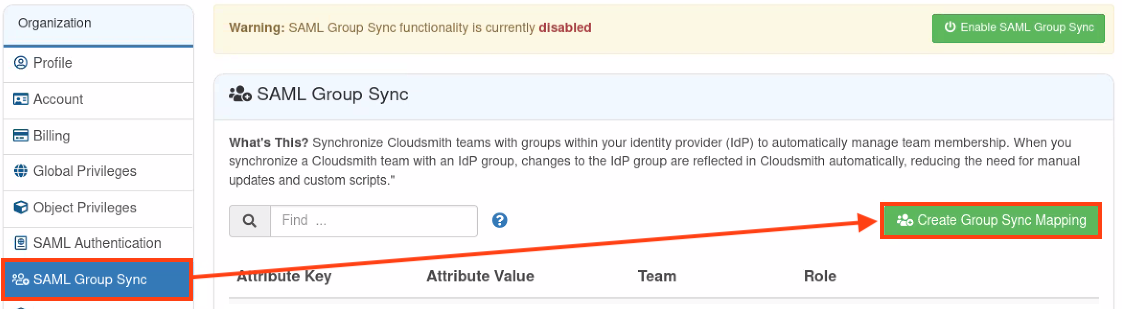
Create Group Sync Mapping Button
You are then presented with the "Create Mapping" form:
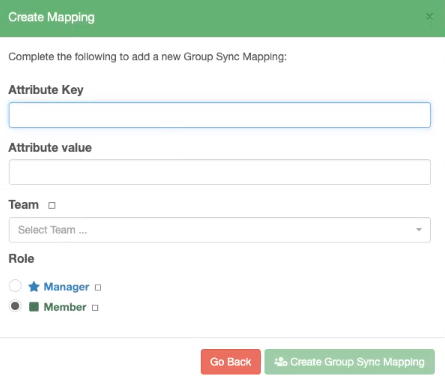
Create Mapping Form
Here you can define the following:
| Field | Description |
|---|---|
| Attribute Key | The Attribute name from your Identity Provider that you use to define groups |
| Attribute Value | The name of the group from your Identity Provider |
| Team | The team in your Cloudsmith Organization that you want this group mapped to |
| Role | The role will be granted within the Team |
Once you have configured your mappings and verified the values are correct, you can then enable the mapping functionality by clicking "Enable SAML Group Sync":
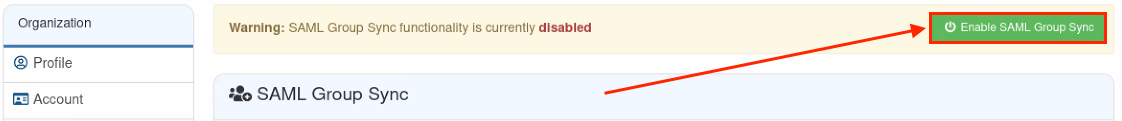
Enable SAML Group Sync Button
Updated 5 months ago
