Vulnerability Policy
Vulnerability Policies enable you to set the acceptable severity threshold for vulnerabilities within your organization. You can create several policies at different levels and determine the actions to take when a package returns a vulnerability level that meets or exceeds a specified threshold.
This feature is useful when you want to either flag or automatically quarantine a package based on the level of vulnerability detected.
Supported Package formats
Vulnerability scanning and vulnerability policies are supported for the following package formats:
View Vulnerability Policies
To manage vulnerability policies in your organization, go to your organization's "Settings" page and select "Vulnerability Policy" from the left-hand menu.
Deactivating a policy is not currently supported, so any policy created will remain active until deleted.
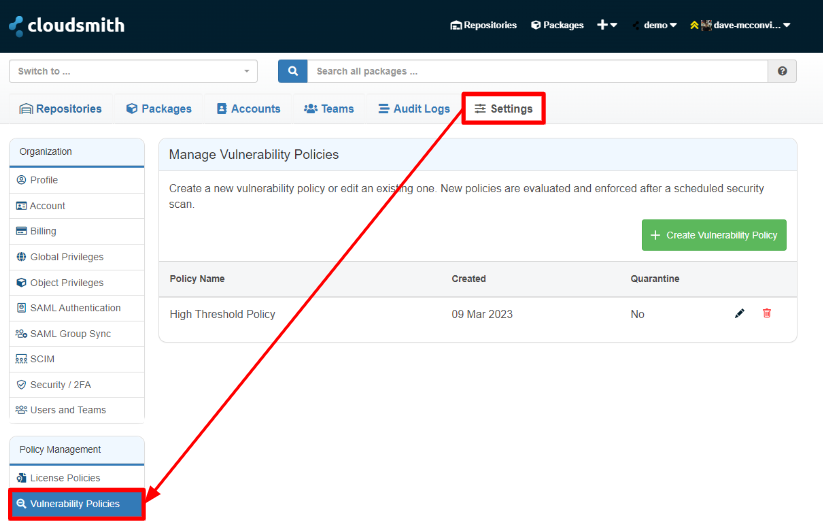
View Vulnerability Policies
Create Vulnerability Policy
To create a new vulnerability policy, click "Create Vulnerability Policy."
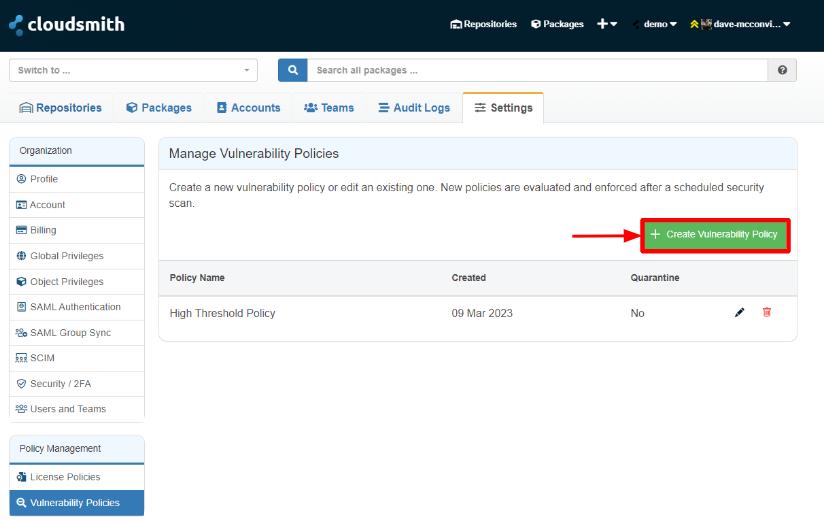
Create Vulnerability Policy Button
You are then presented with the “Create Vulnerability Policy” form:
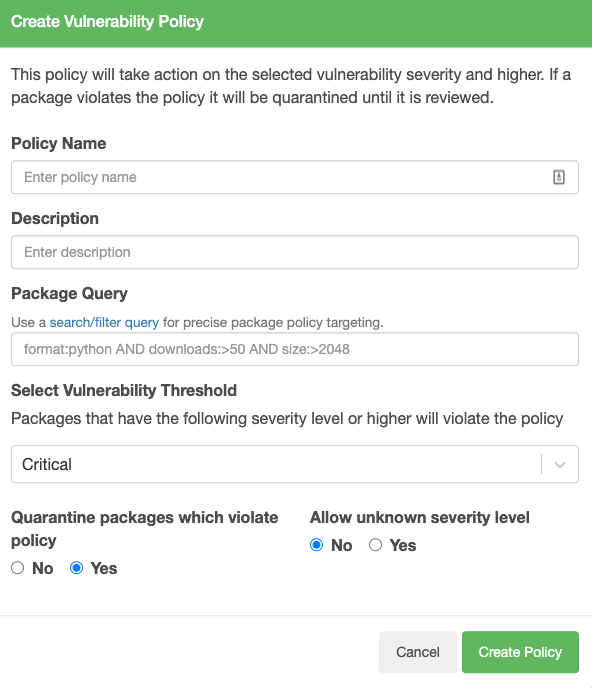
Create Vulnerability Policy Form
Here you can define the following:
Policy Name | A display name for the Vulnerability Policy. |
Description | A description of the Vulnerability Policy. |
Package Query | A search query that you can use to target this policy at a specific repository, package format or package name. See Searching / Filtering for more details on the available fields you can filter on |
Select Vulnerability Threshold | The vulnerability threshold for the policy. Following a package security scan, if a vulnerability matching or exceeding this value is returned, the package will be in violation of the policy. Vulnerability thresholds are based on the following CVSS v3.1 severity ratings: |
Quarantine packages which violate policy | If set to "Yes", any package that has a vulnerability equal to or higher than the threshold will be flagged and automatically quarantined. If set to "No", packages that violate the policy will only be flagged, but they will not be automatically quarantined. |
Allow Unknown severity level | Vulnerabilities may have no CVSS score or severity rating, in which case the severity level is categorized as "Unknown". This setting determines whether or not the Vulnerability Policy should be applied to packages which have vulnerabilities in that category. If set to "Yes", a package with vulnerabilities of an unknown severity level will not be considered to be in violation of the policy. If set to "No", a package with vulnerabilities of an unknown severity level will be considered to be in violation of the policy and the configured policy actions will be taken. |
Once saved, the policy is enabled across your organsization, and the vulnerability policy check is performed on a package every time it undergoes a security scan.
Packages are automatically security scanned on upload and subsequent security scans can be triggered manually via the Web UI, and the Cloudsmith API. See [Security Scanning] for further details on our security scanning feature.
Policy Violation Notification
When a package violates a vulnerability policy a warning is displayed within the UI:
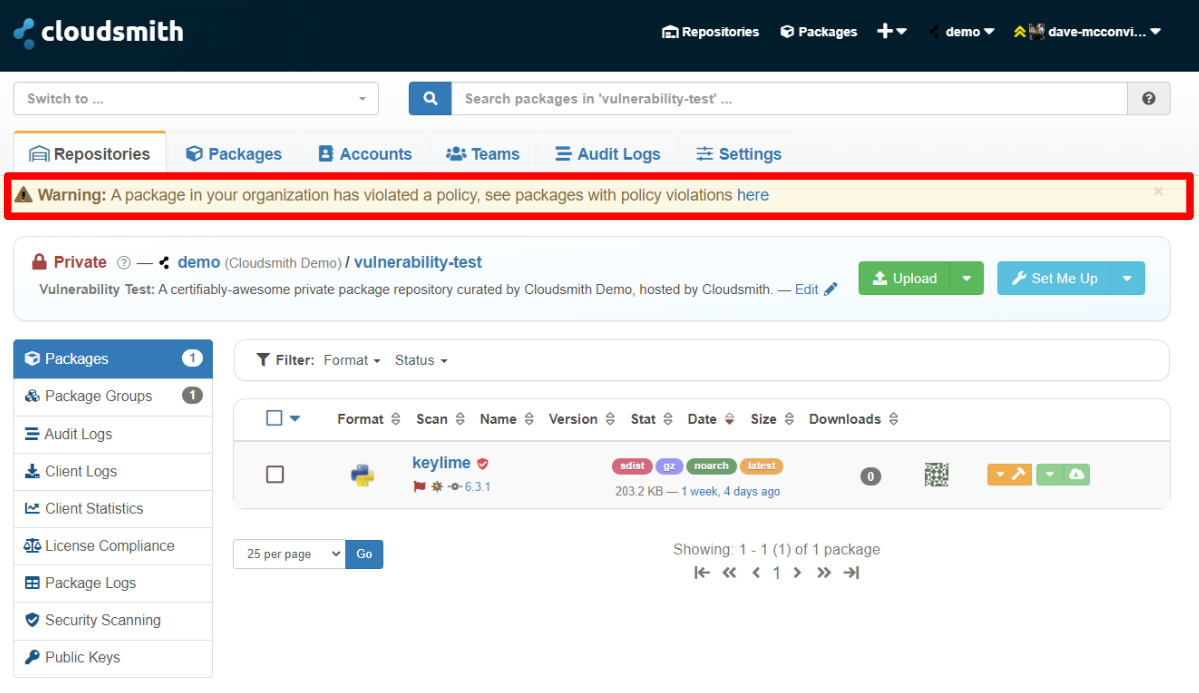
Vulnerability Violation Warning
Clicking the link within this warning, displays a custom search page, displaying all packages with policy violations:
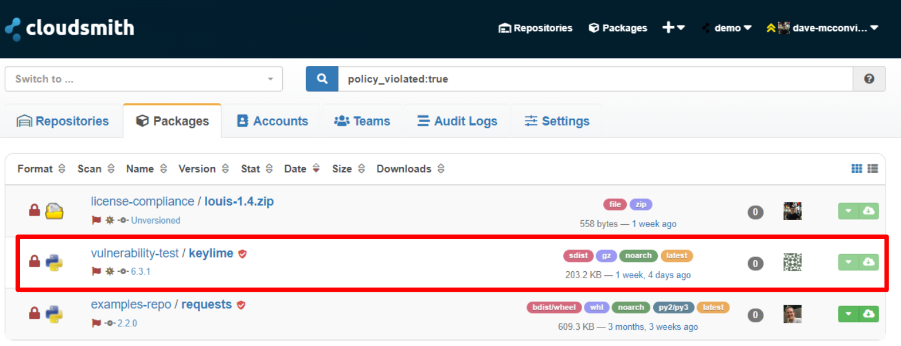
Policy Violation List
You can view this violation list at any time using our package search (link) feature and setting the filter to
policy_violated:truefor all policy violations, orvulnerability_policy_violated:trueto only display vulnerability policy violations.
Policy Violation Identifiers
Within a repository, packages with policy violations are identified with the Policy Violation and Quarantined icons.
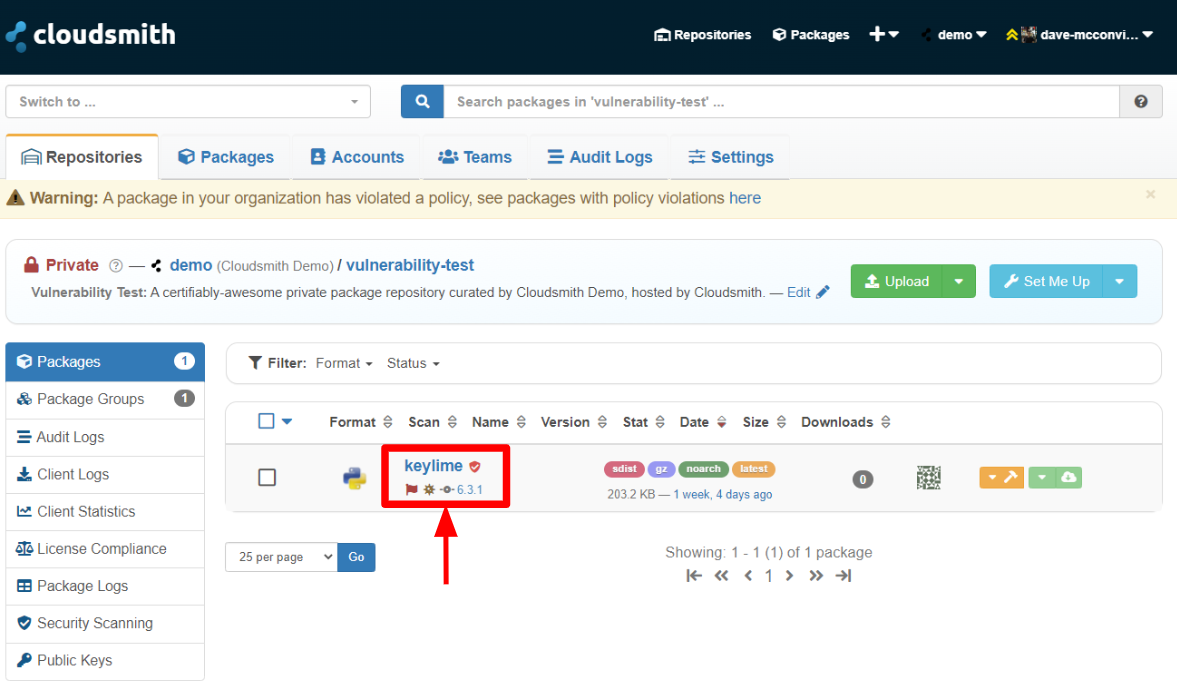
Policy Violation Indicators
 | Policy Violation | This package is in violation of a vulnerability policy. Click on the package to view more details. |
Quarantined | This package has been quarantined, downloads will be blocked until the package is released from quarantine. Reason given: the package was quarantined as a result of a policy violation | |
 | Security Vulnerability Detected | The security scan has detected vulnerabilities within this package. |
Clicking on the package name displays the Package view page, which provides details on the policy that has been violated.
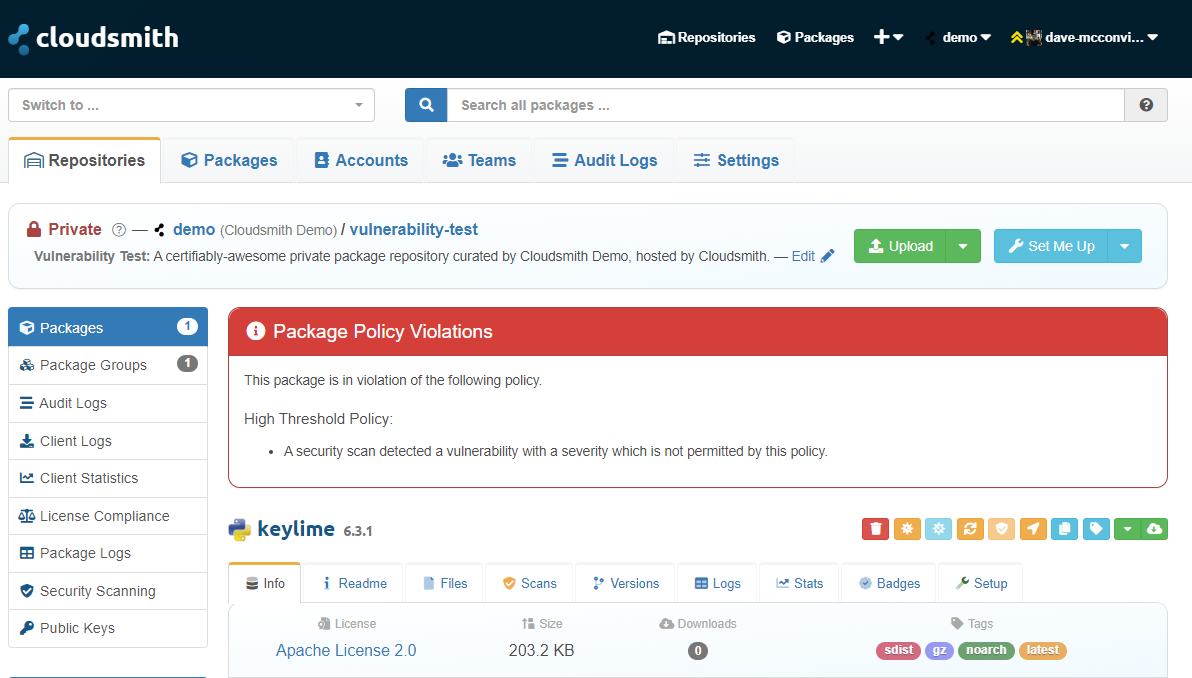
Package Logs
Logs of policy violations and quarantining actions are also displayed within the Package Logs page:
Hover over the “policy violation” text to display additional details on the policy and vulnerability violation.
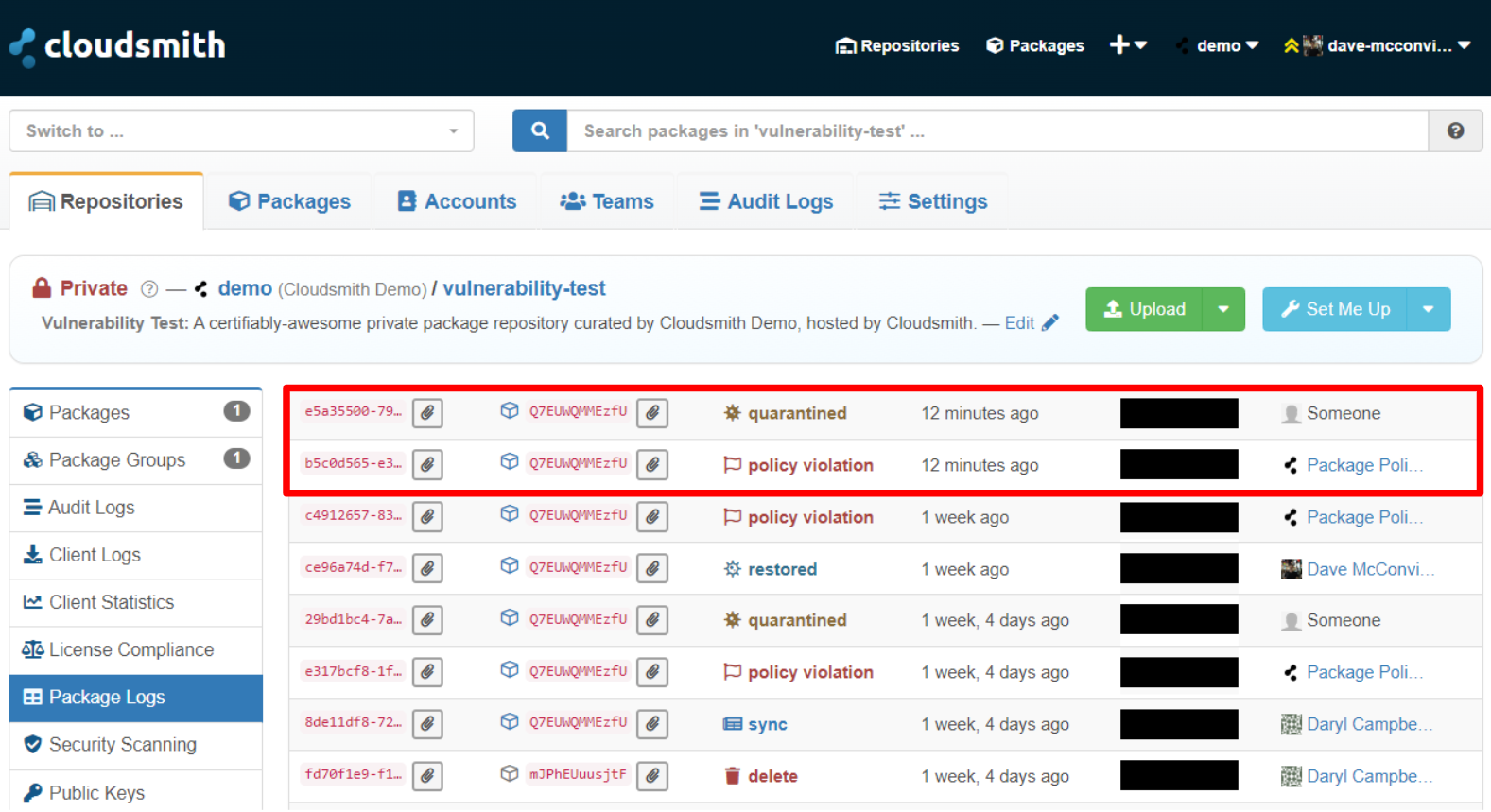
Restore a package that violates a policy
To remove a policy violation, you have three options:
- Upgrade the package to a version that has resolved the security vulnerability.
- Edit the vulnerability policy to lower the threshold below the violated level. A manual rescan of the package is required to remove the policy violation flag and the package must also be manually released from quarantine.
- Use the restore functionality to remove the package from quarantine. Keep in mind, however, that subsequent security scans may return the package to quarantine. See Release from quarantine for instructions on restoring a package from quarantine.
Updated 4 months ago


