Geo/IP Rules
If you need to add physical location security to your package management, then Geo/IP Restriction is what you need. You can restrict or grant access to your packages based on geographical location, IP ranges or specific IP addresses.
You could, for example, use these restrictions to only allow access from your organization VPN IP address(es) or from specific organization locations/sites.
Enabling and Configuring Geo / IP Restrictions
These restrictions only apply to downloads-based traffic and do not apply to web-based traffic.
- The deny lists are applied before the allow lists and therefore take precedence.
- Geo-based restrictions are also applied before IP-based restrictions.
- The first rule matching the incoming traffic is applied.
To enable IP restrictions for uploads please see API-Key
To enable Geo / IP restrictions, select "Geo/IP Rules" from the left menu on a repository detail page, then click the green "Enable Geo /IP" button on the right side.
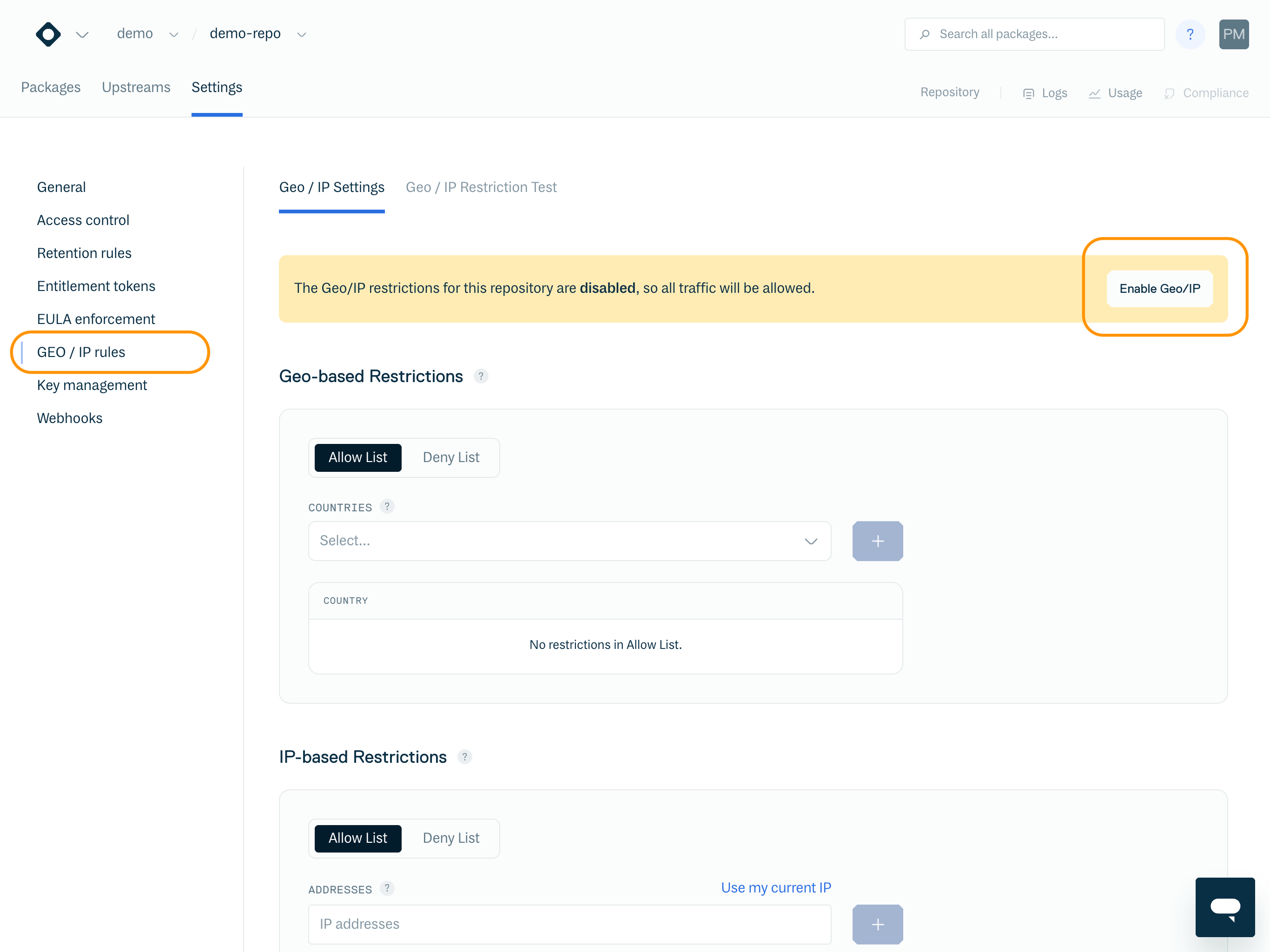
Geo / IP Restrictions configuration page
Geo-based Restrictions
Use the "Deny" or "Allow" fields under "Geo-based Restrictions" to specify the geographic regions/countries that you wish to block or allow respectively. When you start to type the name of a region or country in these fields you will be offered a matching selection from the drop-down list. You can add multiple regions/countries to block or allow:
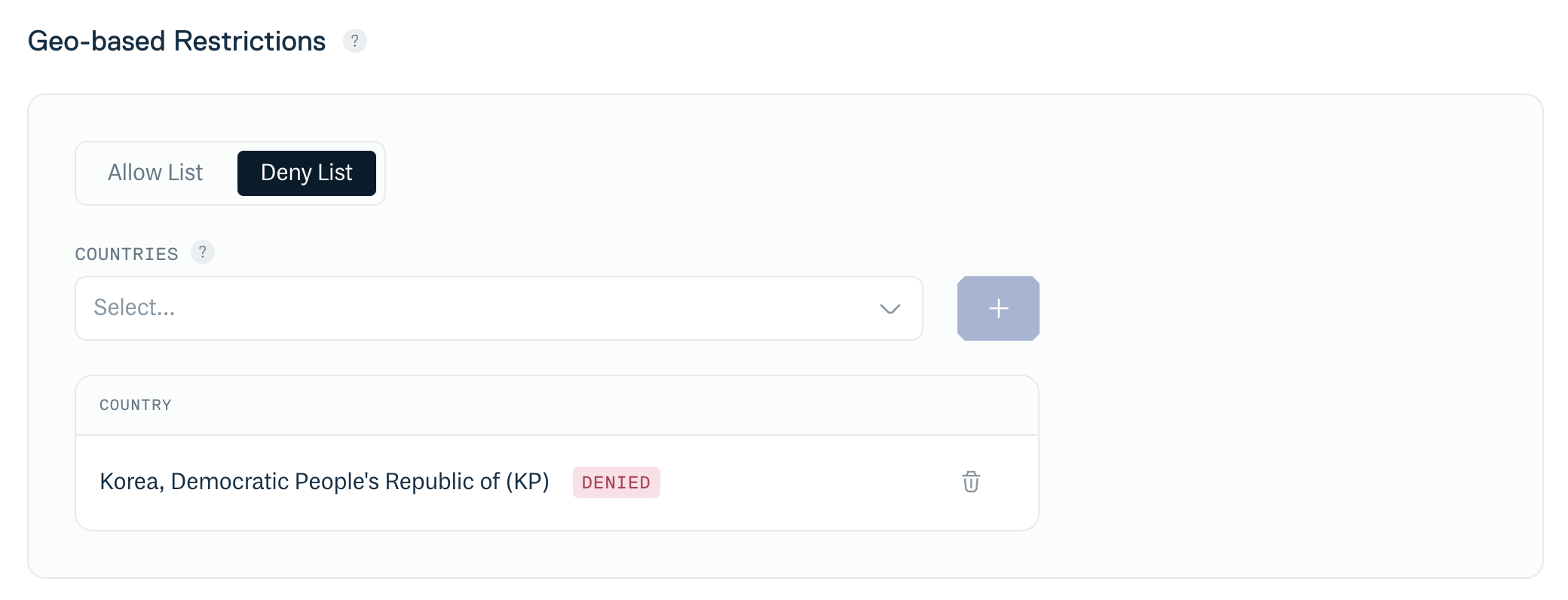
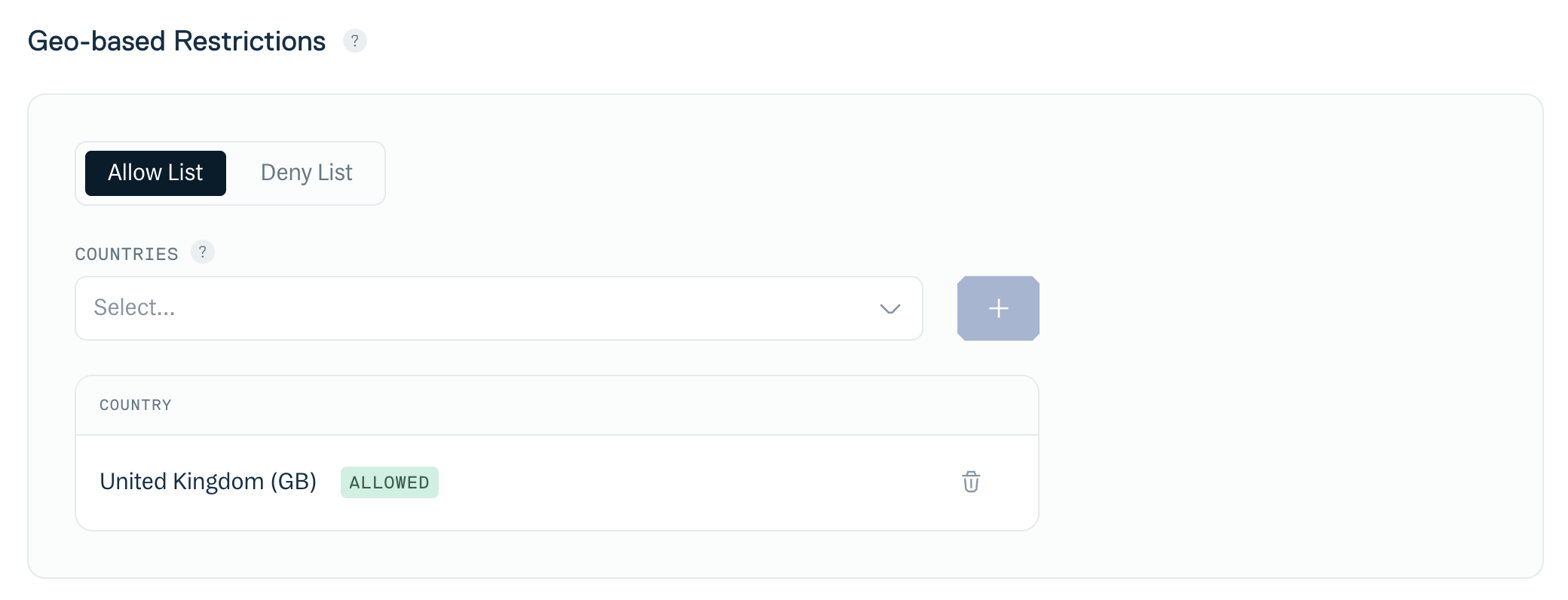
Geo-based restrictions - region/country entry
If the region/country can't be resolved from an IP address (e.g for an internal or private IP), then setting this will have no effect.
IP-based Restrictions
Use the "Deny" or "Allow" fields under "IP-based restrictions" to specify the IP addresses / CIDRs that you wish to block or allow. You can enter multiple IP addresses / CIDRs in each field:
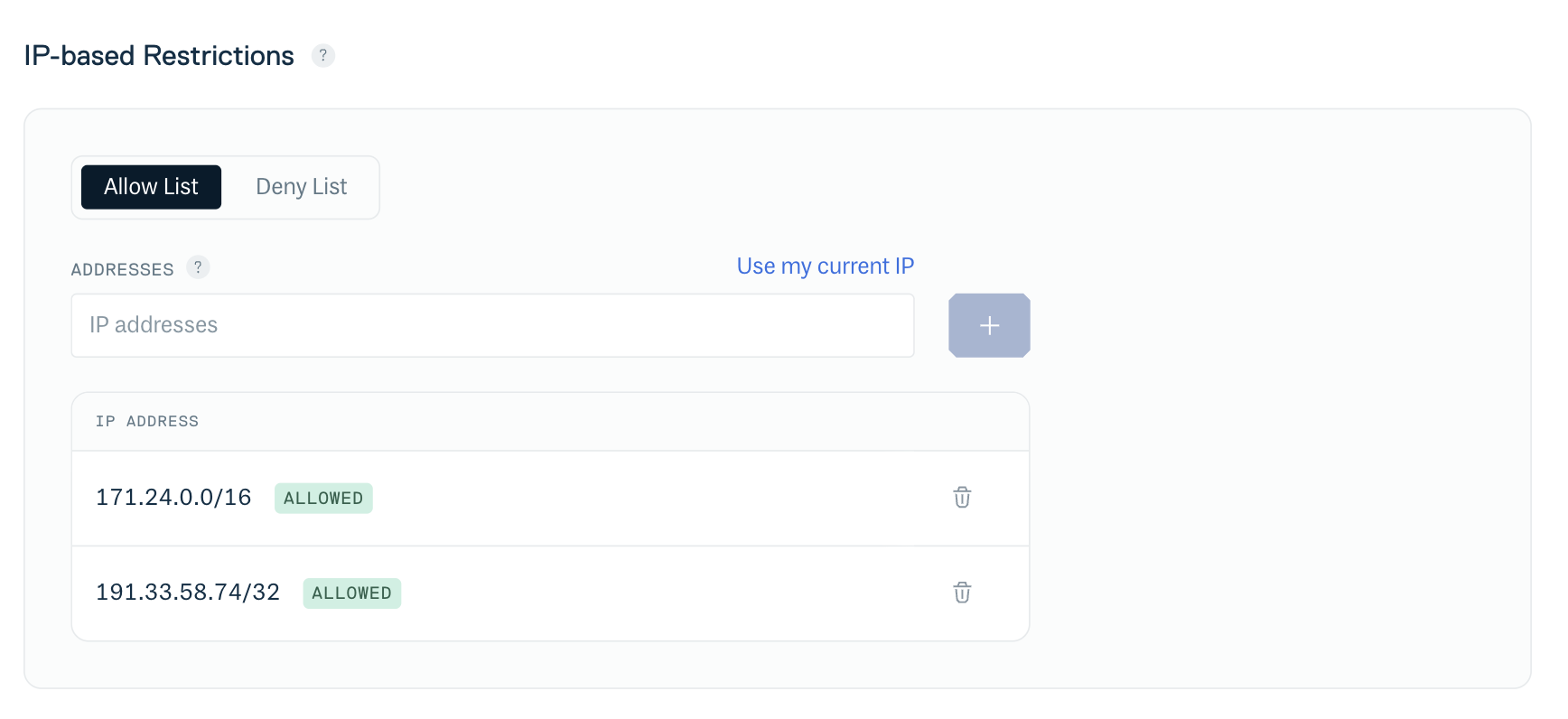
IP-based restrictions - IP address / CIDR entry
Updated 4 months ago
