Audit Logs
Organization Audit Logs provide a log of events across your organization, such as creating/deleting a repository or modifications to repository settings/configuration.
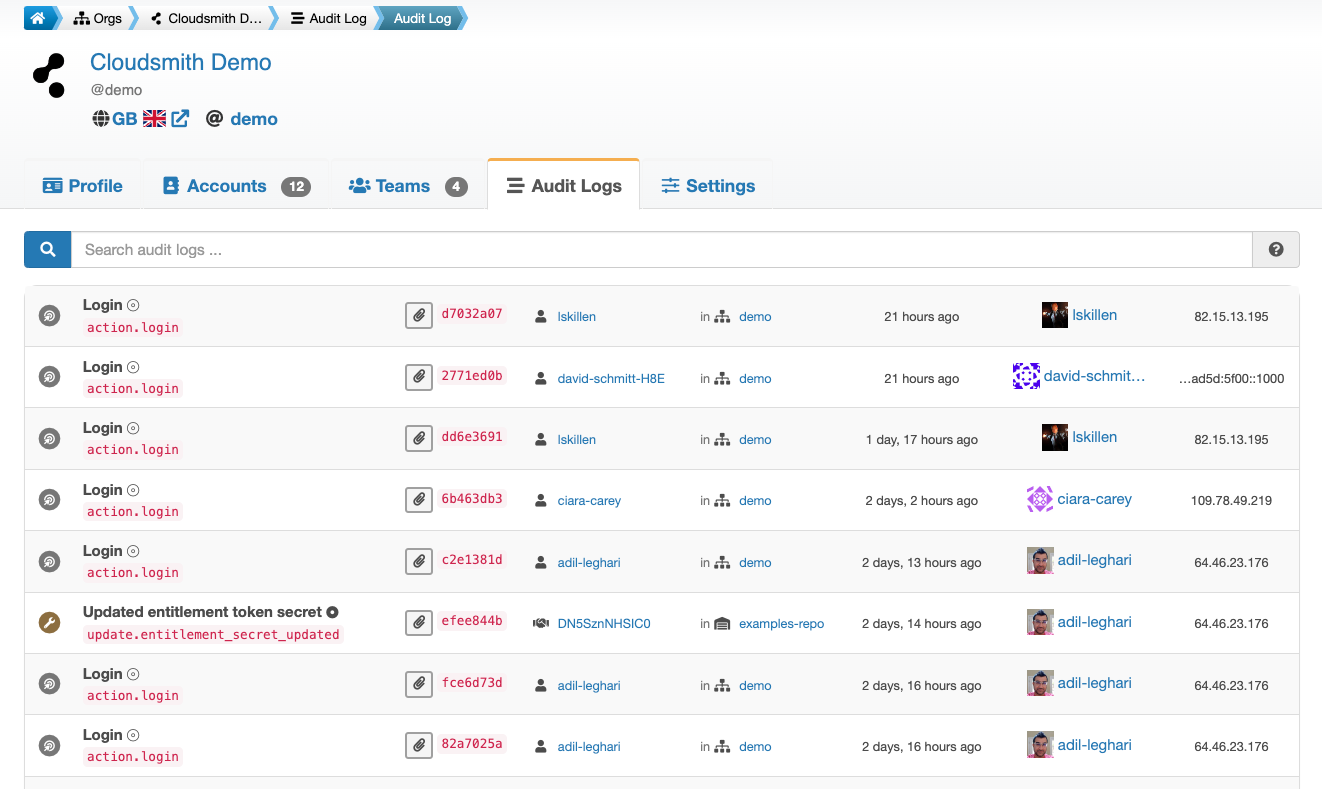
Organization Audit Logs
Key Concepts:
Each entry in the log represents an event or a state change and consists of four main components.
- Actor: The object that performed the Action, such as a User, Service Account or System
- Verb: The verb (phrase) identifying "what_happened", such as
login,retention_settings_changedortoken_created - Action Object: The object which was created, deleted or updated by the action.
- Target: (Optional) The object within which the Action was performed, such as a repository or account
Searching / Filtering
You can Search and Filter the Audit Log using the search box at the top. You can also use boolean logic (e.g. AND/OR/NOT) for complex search queries.
Search Terms
| Search By | Search Terms Example |
|---|---|
| Actor | actor:some-user |
| Actor Kind | actor_kind:user (user)actor_kind:service_account (service account)actor_kind:system |
| Event Time | event_at:>"1 day ago"event_at:<"June 21, 2022 EST" |
| Event Kind | event_kind:action (action)event_kind:create (create)event_kind:read (read)event_kind:update (update)event_kind:delete (delete) |
| Event (Fuzzy) | event:api_key (api key events)event:entitlement (entitlement events)event:login (login events)event:package (package events)event:retention (retention events)event:service_account (service account events) |
Field type modifiers (depending on the type, you can influence behaviour)
-
For all queries, you can use:
~foofor negation -
For string queries, you can use:
^footo anchor to start of term
foo$to anchor to end of term
foo*barfor fuzzy matching -
For number/date queries, you can use:
>foofor values greater than
>=foofor values greater / equal
<foofor values less than
<=foofor values less / equal
Updated almost 2 years ago
